Author: Navjot Singh, Cloud Engineer
We’re familiar with the term DevOps, right? but, what is GitOps? Is it similar to DevOps? different? or the next step towards a modern deployment!
It can be said that GitOps is the next step from DevOps, while DevOps focuses more on the methodologies and ways to achieve the desired task. GitOps focuses on the centralized tool GIT. Let’s go over a proper definition of GitOps.
What is GitOps?
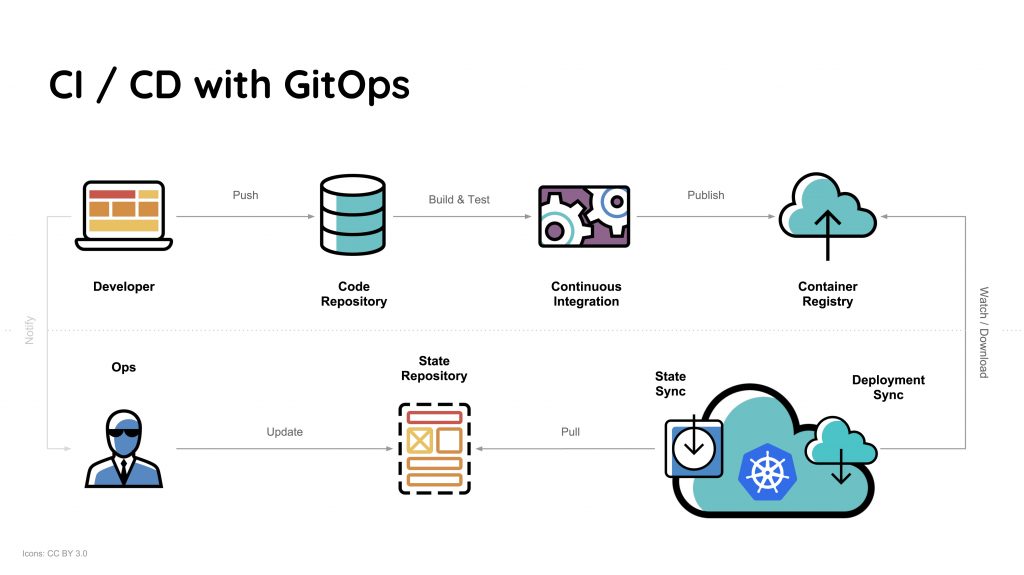
GitOps is a way of implementing Continuous Deployment for cloud-native applications. It focuses on a developer-centric experience when operating infrastructure, by using tools developers are already familiar with, including Git and Continuous Deployment tools.
The core idea of GitOps is having a Git repository that always contains declarative descriptions of the infrastructure currently desired in the production environment and an automated process to make the production environment match the described state in the repository. If you want to deploy a new application or update an existing one, you only need to update the repository – the automated process handles everything else. It’s like having cruise control for managing your applications in production.
Workflow of GitOps
GitOps follows has a simple workflow to automate the Deployments:
- Developer commits & pushes the updated code to the Git repository.
- GitOps tool installed in our Kubernetes cluster detects from the commit history of Git.
- GitOps tool tries to sync the desired configurations in the git repository to current configurations in the Kubernetes cluster.
In the above workflow, we can see a newly introduced term GitOps tool. What are the GitOps tools? Well, GitOps tools are the tools that work in sync with the Git repository to track the changes and apply the same on the Kubernetes cluster.
GitOps tools available at the moment:
- ArgoCD: A GitOps operator for Kubernetes with a web interface
- Flux: The GitOps Kubernetes operator by the creators of GitOps — Weaveworks
- Gitkube: A tool for building and deploying docker images on Kubernetes using
git push - JenkinsX: Continuous Delivery on Kubernetes with built-in GitOps
- Terragrunt: A wrapper for Terraform for keeping configurations DRY, and managing remote state
- WKSctl: A tool for Kubernetes cluster configuration management based on GitOps principles
- Helm Operator: An operator for using GitOps on K8s with Helm
- werf: A CLI tool to build images and deploy them to Kubernetes via a push-based approach.
We’ll be using Flux, ArgoCD for CD, and Github Actions for the CI process.
So, our Continuous Deployment is automated and is integrated within Kubernetes Cluster which is Azure Kubernetes Service in our case.
Let’s get started
- Create AKS Cluster
az aks create -n aks-gitops -g navjot-rg –node-count 3 –generate-ssh-keys
- Connect to AKS Cluster
az aks get-credentials -n aks-gitops -g navjot-rg
- List Kuberentes Nodes
kubectl get nodes
FluxCD
As of now, Our Kubernetes cluster is empty, nothing is been deployed yet. Let’s install FluxCD into the cluster following the steps below:
- Create a Namespace
kubectl create ns flux
- export a variable for Github Username
export GHUSER=”navjots35″
- Install FluxCD and Sync the Git URL and Path from which the YAML files will be deployed.
fluxctl install <span class="se">\</span>
–git-user<span class="o">=</span><span class="si">${</span><span class="nv">GHUSER</span><span class="si">}</span> <span class="se">\</span>
–git-email<span class="o">=</span><span class="si">${</span><span class="nv">GHUSER</span><span class="si">}</span>@users.noreply.github.com <span class="se">\</span>
–git-url<span class="o">=</span>git@github.com:<span class="si">${</span><span class="nv">GHUSER</span><span class="si">}</span>/ContosoCrafts <span class="se">\</span>
–git-path<span class="o">=</span>manifests <span class="se">\</span>
–namespace<span class="o">=</span>flux <span class="p">|</span> kubectl apply -f –
Let’s understand this, we’ve multiple parameters here, focus on `git-url` and `git-path`. I’ve replaced the URL with my repository and the path with the manifests folder where YAML files exist. FluxCD needs manifest files in-order to replicate the desired configurations (Git Repo) to Current Configurations (Kubernetes Cluster).
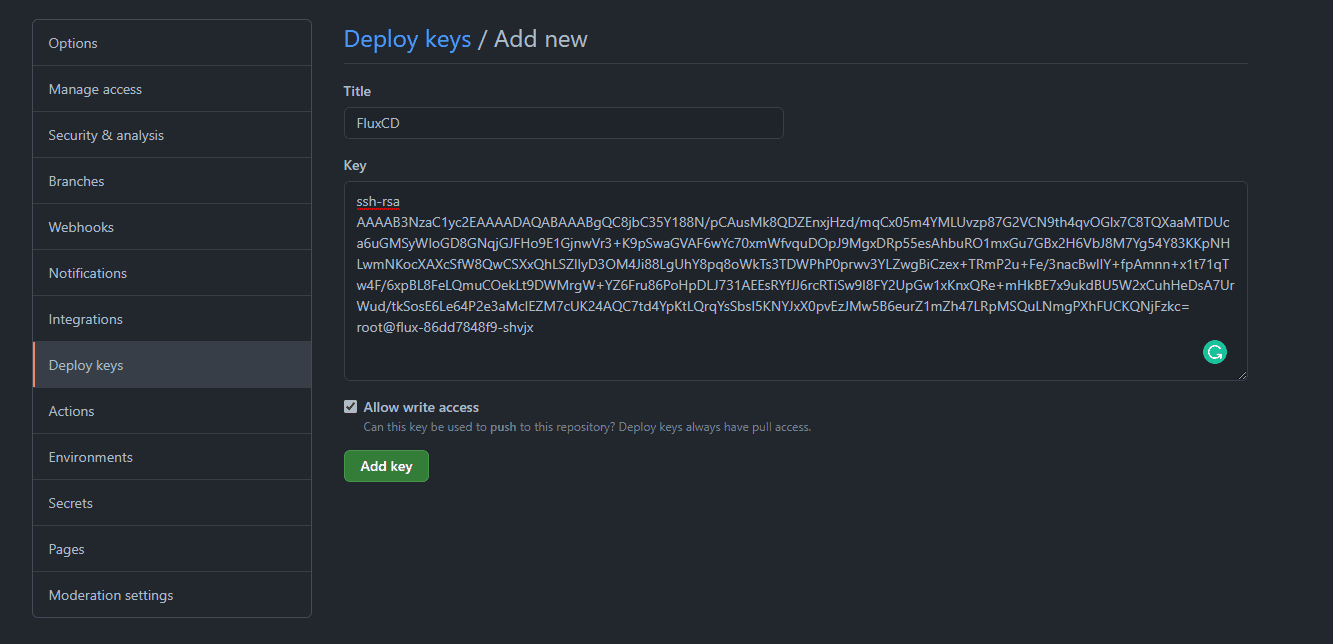
We’re done with the installation but we need to give FluxCD permissions to read & write from the Git Repo to Kubernetes Cluster. Generate SSH key from Fluxctl command to and add it to git repo under deploy keys.
- Generate SSH Keys using Fluxctl
Fluxctl identity –k8s-fwd-ns=flux
- Copy this SSH Key and navigate to your Git Repo –> Under Settings –> Deploy Keys. Make sure to give “Allow write access” and Add the key.
- Now, hit back to the Terminal and sync the git repo
fluxctl sync –k8s-fwd-ns=flux
You should get output similar to this.
Now, you should see the resources deployed automatically. Make a change to a code, build that and push to the git repo and check the flux pod logs to see any changes, Fluxctl checks changes after every 5 minutes to replicate those changes into the cluster.
ArgoCD
Argo CD is a declarative, GitOps continuous delivery tool for Kubernetes. ArgoCD is another GitOps tool that helps in implementing a GitOps workflow across the Kubernetes environment. Unlike FluxCD, ArgoCD comes with a Web UI to manage workloads.
- Install ArgoCD into the Cluster.
kubectl create namespace argocd
kubectl apply -n argocd -f https://raw.githubusercontent.com/argoproj/argo-cd/stable/manifests/install.yaml
- Expose the ArgoCD UI
kubectl patch svc argocd-server -n argocd -p <span class="s1">'{"spec": {"type": "LoadBalancer"}}'</span>
You can either expose it via load balancer or do the port forwarding to local system.
The initial password for the admin account is auto-generated and stored as clear text in the field password in a secret named argocd-initial-admin-secret in your Argo CD installation namespace. You can simply retrieve this password using kubectl:
kubectl -n argocd get secret argocd-initial-admin-secret -o <span class="nv">jsonpath</span><span class="o">=</span><span class="s2">"{.data.password}"</span> <span class="p">|</span> base64 -d
Enter username as admin and password as retrieved from the above command.
Let’s setup our Github Repository to sync and replicated the configurations over to our cluster.
- Navigate to Settings –> Repositories
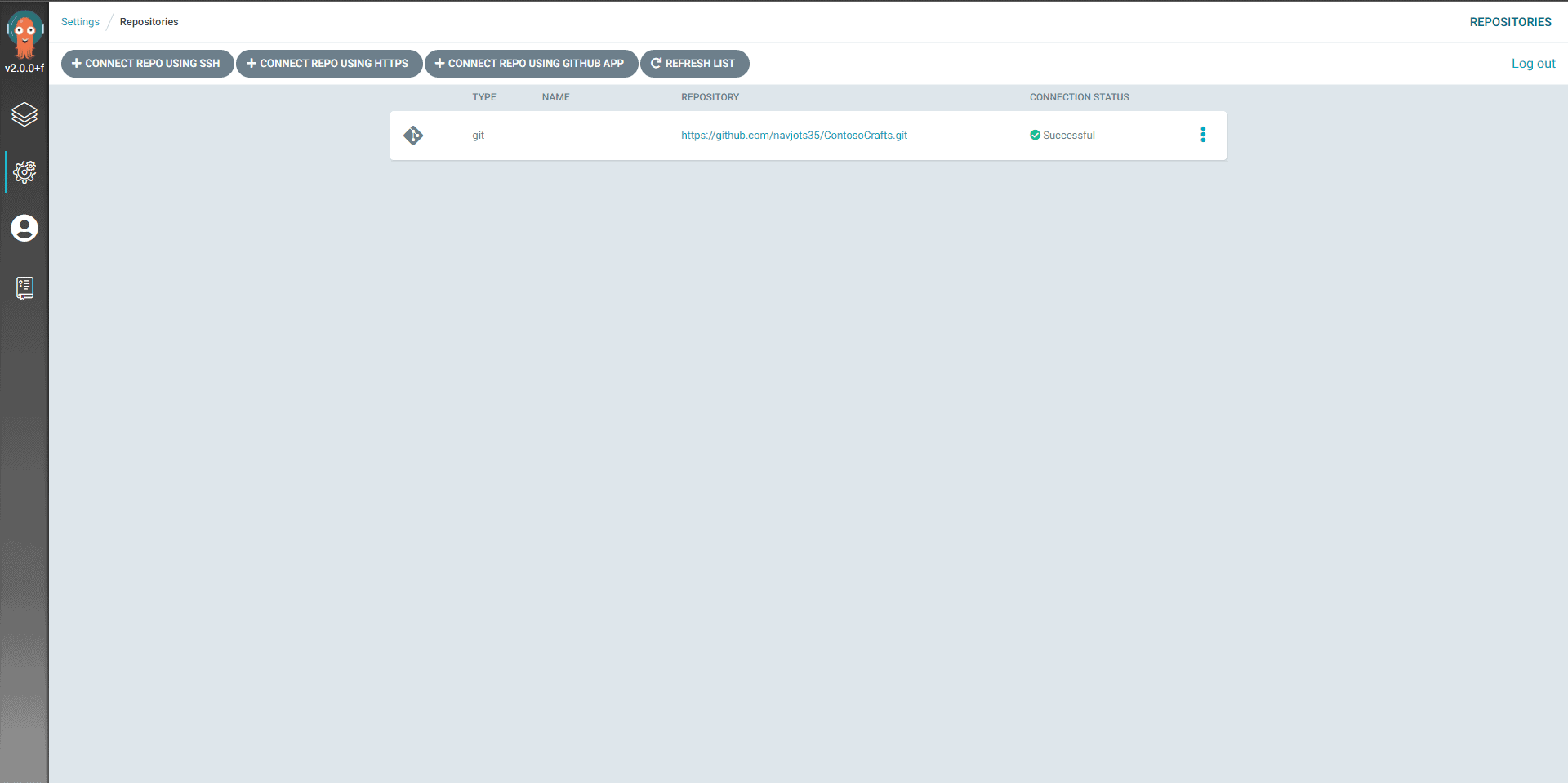
- Connect Repo using HTTPS –> Add your Git URL and hit save. It’ll show connection status as Successful.
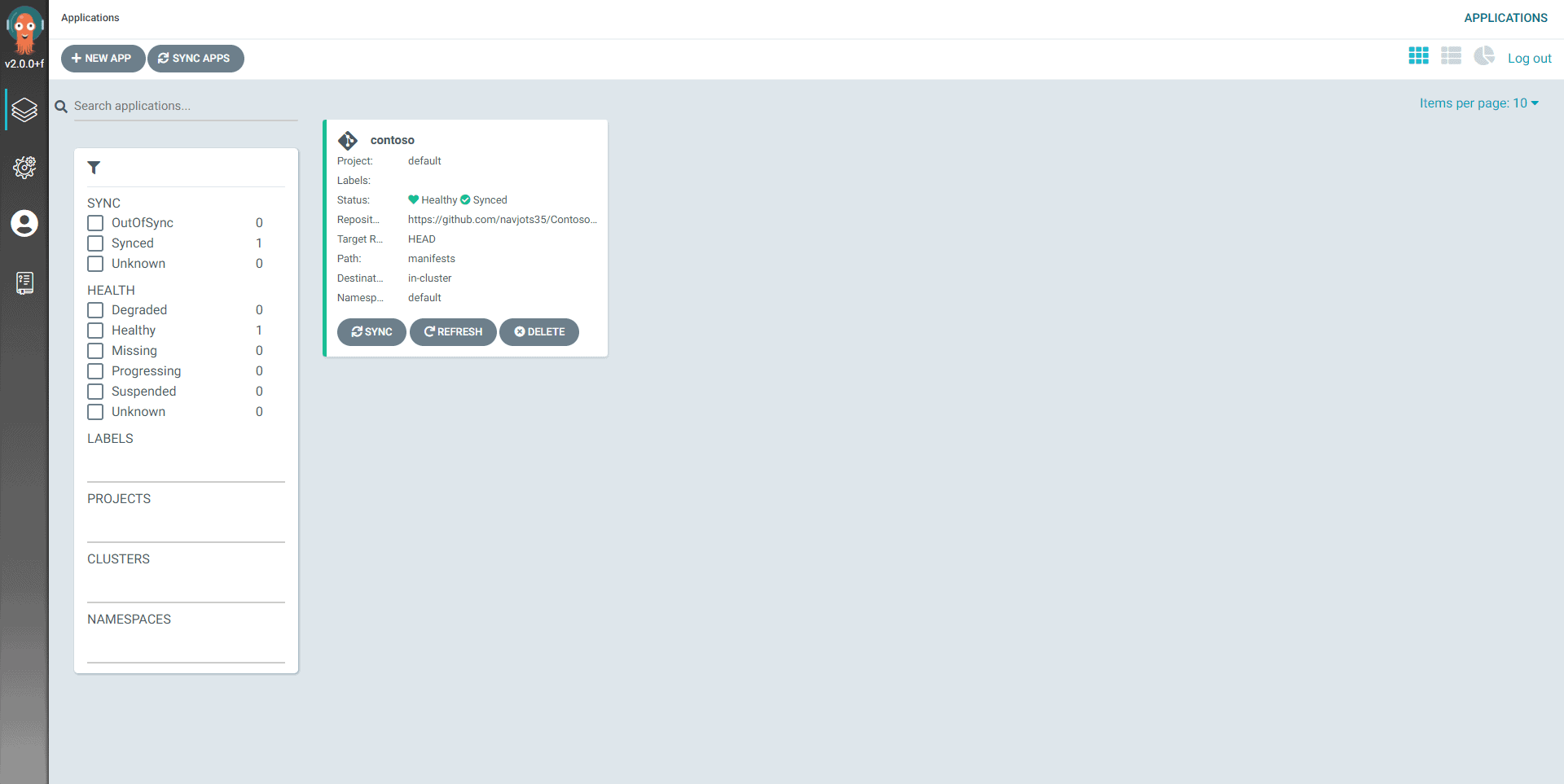
- Create a New App
- Configure the New App settings
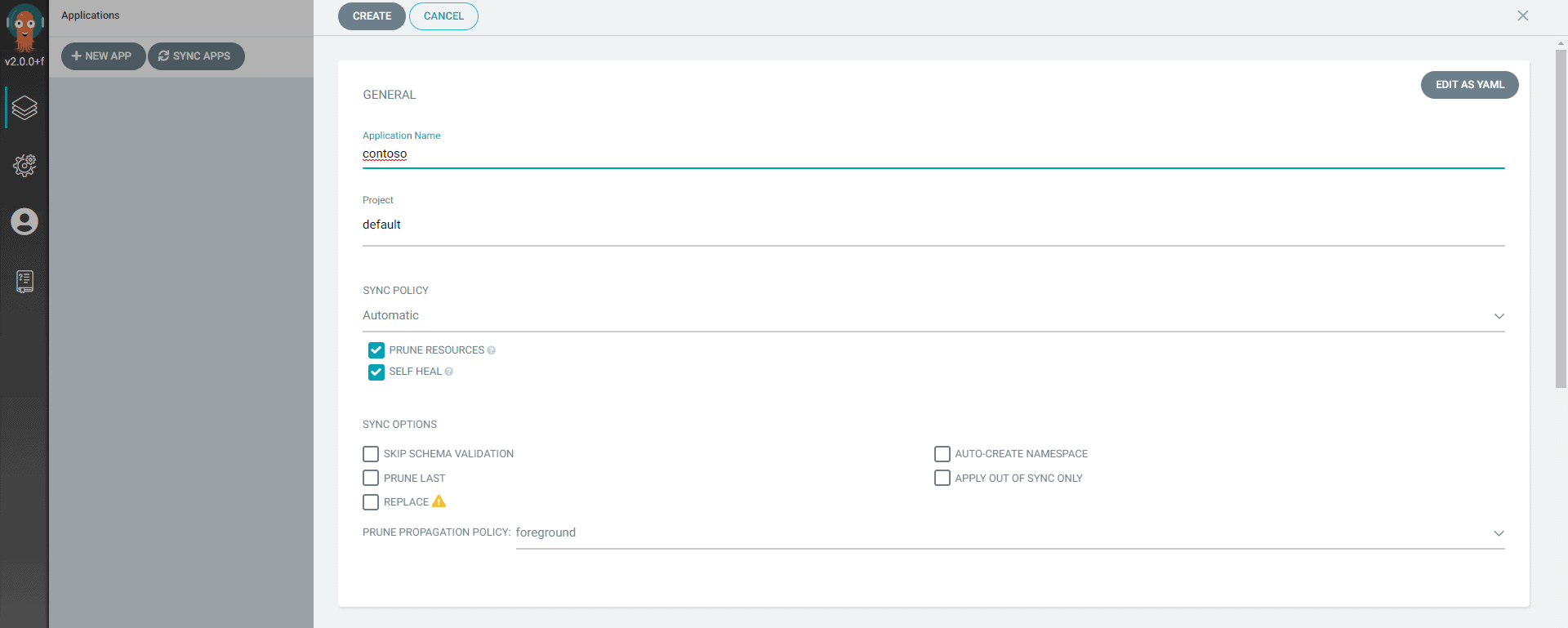
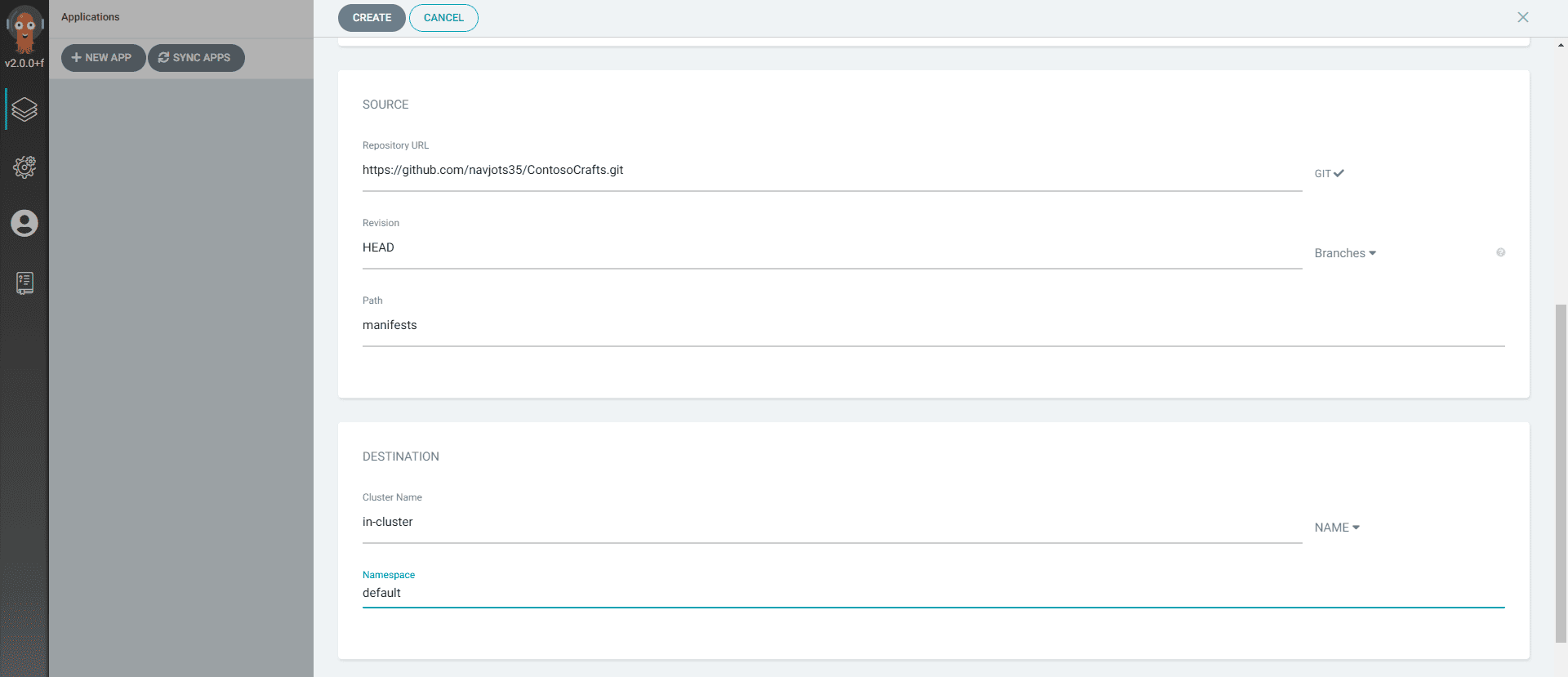
- In the above config, we’ve mentioned the path of our manifests files, this step is necessary without this ArgoCD won’t create a new application if it’s unable to find the manifests files.
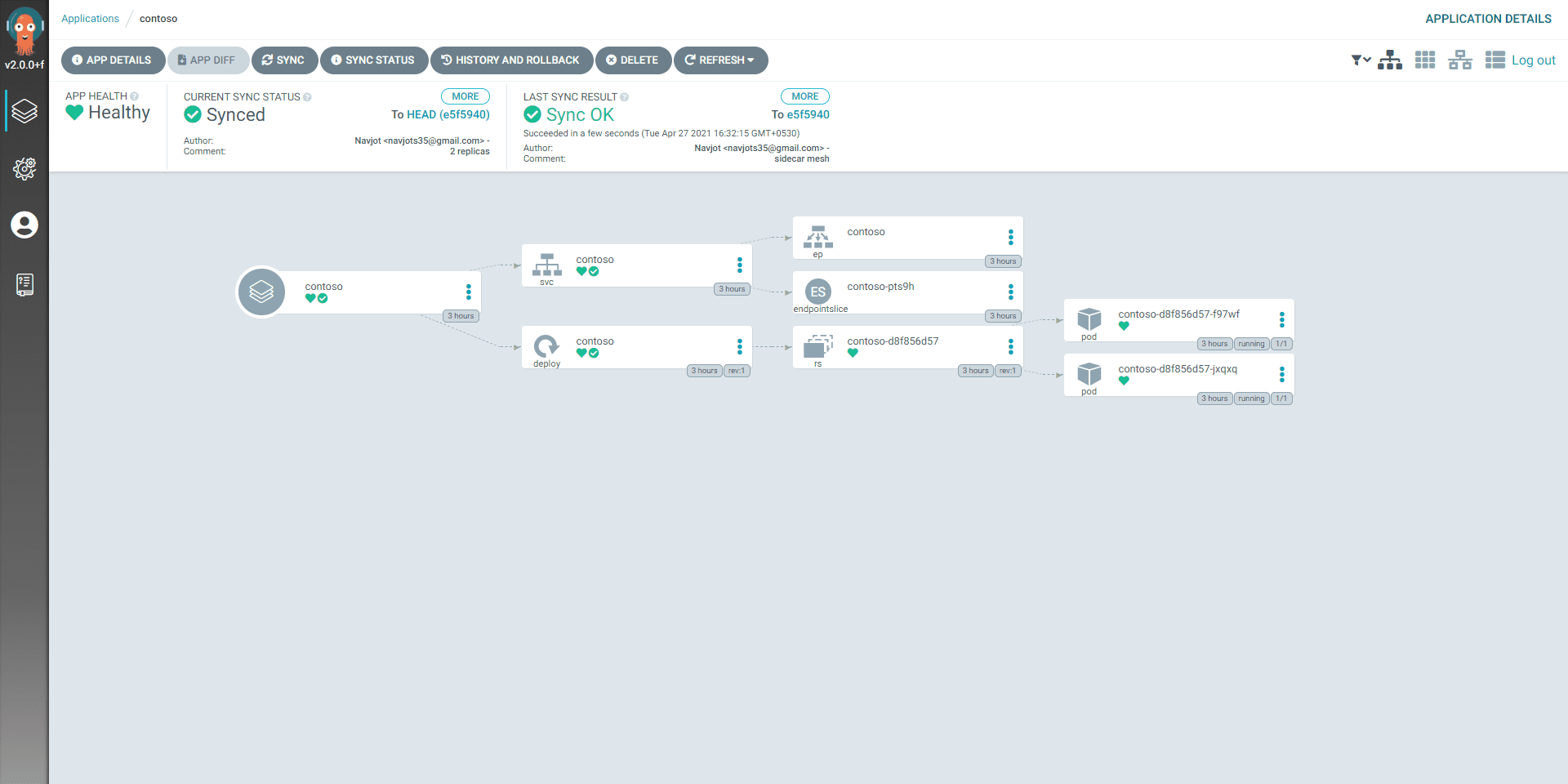
We can see our application is successfully synced with our cluster. Every change that’s been pushed to git repo will be synced into the cluster. We can also do the manual sync process.