This blog gives a brief overview of newly service added in Microsoft Azure i.e. Azure Sentinel (In preview while writing this blog).
Azure Sentinel provides intelligent security analytics at cloud scale for your entire enterprise. Azure Sentinel makes it easy to collect security data across your entire hybrid organization from devices, to users, to apps, to servers on any cloud. It uses the power of artificial intelligence to ensure you are identifying real threats quickly and unleashes you from the burden of traditional SIEMs by eliminating the need to spend time on setting up, maintaining, and scaling infrastructure. Since it is built on Azure, it offers nearly limitless cloud scale and speed to address your security needs. Traditional SIEMs have also proven to be expensive to own and operate, often requiring you to commit upfront and incur high cost for infrastructure maintenance and data ingestion. With Azure Sentinel there are no upfront costs, you pay for what you use.
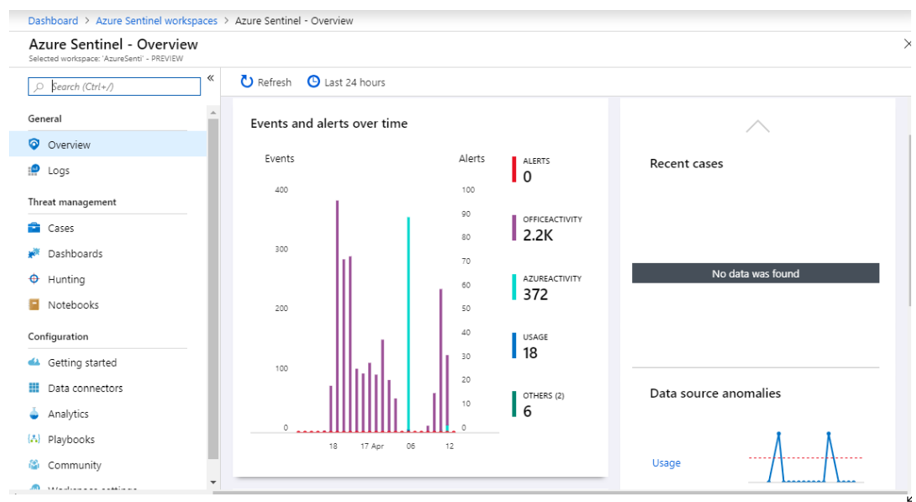
Let’s look at how Azure Sentinel will help you deliver cloud-native security operations:
Collect data across your enterprise easily- With Azure Sentinel you can aggregate all security data with built-in connectors, native integration of Microsoft signals, and support for industry standard log formats like common event format and syslog. In just a few clicks you can import your Microsoft Office 365 data for free and combine it with other security data for analysis. Azure Sentinel uses Azure Monitor which is built on a proven and scalable log analytics database that ingests more than 10 petabytes every day and provides a very fast query engine that can sort through millions of records in seconds.
- Analyze and detect threats quickly with AI on your side- Security analysts face a huge burden from triaging as they sift through a sea of alerts, and correlate alerts from different products manually or using a traditional correlation engine. That’s why Azure Sentinel uses state of the art, scalable machine learning algorithms to correlate millions of low fidelity anomalies to present a few high fidelity security incidents to the analyst. ML technologies will help you quickly get value from large amounts of security data you are ingesting and connect the dots for you.
- Investigate and hunt for suspicious activities- Graphical and AI-based investigation will reduce the time it takes to understand the full scope of an attack and its impact. You can visualize the attack and take quick actions in the same dashboard.
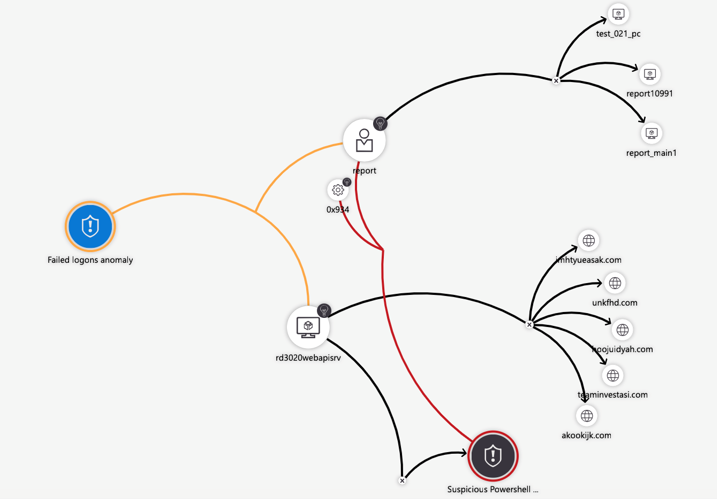
It provides two capabilities that enable you to automate your analysis by building hunting queries and Azure Notebooks that are based on Jupyter notebooks.
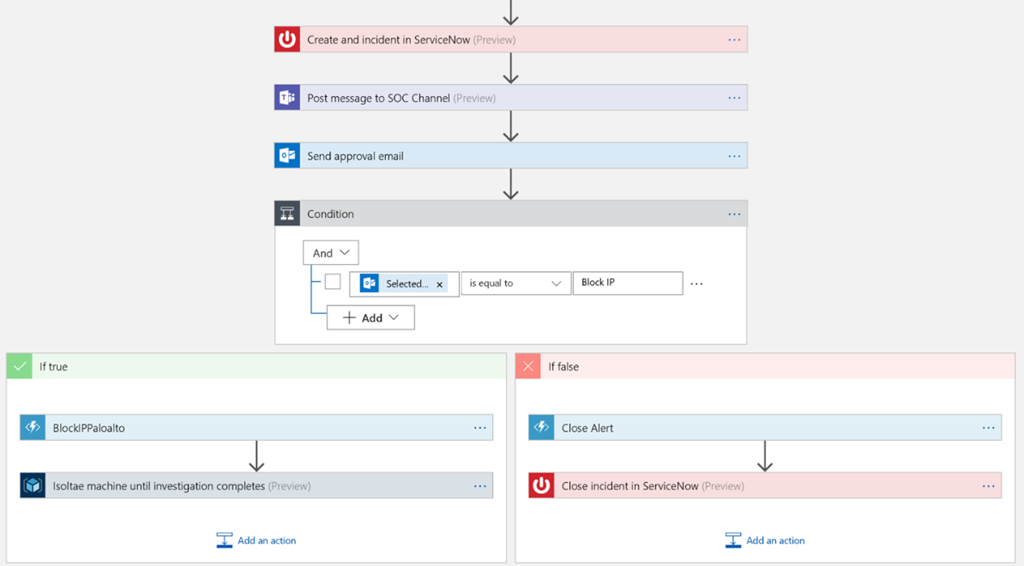
- Automate common tasks and threat response- Azure Sentinel provides built-in automation and orchestration with pre-defined or custom playbooks to solve repetitive tasks and to respond to threats quickly. Azure Sentinel will augment existing enterprise defence and investigation tools, including best-of-breed security products, home-grown tools, and other systems like HR management applications and workflow management systems like Service Now.